
ThinkIQ and UST partner to streamline supply chain and manufacturing processes through cloud-based software that provides materials visibility and traceability.
ThinkIQ and UST partner to streamline supply chain and manufacturing processes through cloud-based software that provides materials visibility and traceability.

What kind of guidance is available to help you defend your industrial control system (ICS)?
What kind of guidance is available to help you defend your industrial control system (ICS)?

Engineering and industrial software provider AVEVA announced an extension of its partnership with Microsoft, focusing on…
Engineering and industrial software provider AVEVA announced an extension of its partnership with Microsoft, focusing on digital transformation in the industrial sector.

The following will introduce how machine vision and object recognition works and how developers are working on making it…
The following will introduce how machine vision and object recognition works and how developers are working on making it easier to integrate for more extensive market adoption.
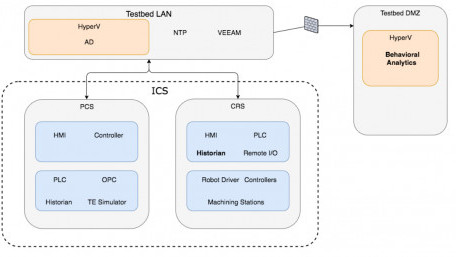
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track…
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track potential security threats.
As digital twinning technology continues to advance, industry leaders are stepping up their innovation efforts to bring…
As digital twinning technology continues to advance, industry leaders are stepping up their innovation efforts to bring together the physical and virtual world.
Volkswagen and Amazon Web Services extend the Volkswagen Industrial Cloud Network to include more companies for…
Volkswagen and Amazon Web Services extend the Volkswagen Industrial Cloud Network to include more companies for optimizing software development and business growth.
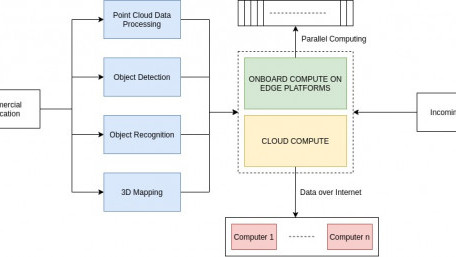
Edge computing and cloud computing both have their place in industrial automation and control systems. Learn about the…
Edge computing and cloud computing both have their place in industrial automation and control systems. Learn about the uses and how far the two technologies have to go before they're universally adopted.

Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility…
Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility plants protected.

Learn all about Digital Twinning, and how this new technique can change the way we do a number of industrial operations!
Learn all about Digital Twinning, and how this new technique can change the way we do a number of industrial operations!

The CyberX platform comprises a series of tools, ranging from perimeter firewalls and conventional ICS/SCADA defenses to…
The CyberX platform comprises a series of tools, ranging from perimeter firewalls and conventional ICS/SCADA defenses to IoT-specific features to provide continuous monitoring and real-time alerting.

Liquid lens and multi-spectral lighting solutions are advancing the manufacturer’s production lines.
Liquid lens and multi-spectral lighting solutions are advancing the manufacturer’s production lines.

Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the…
Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the operational risks, and how are they assessed?
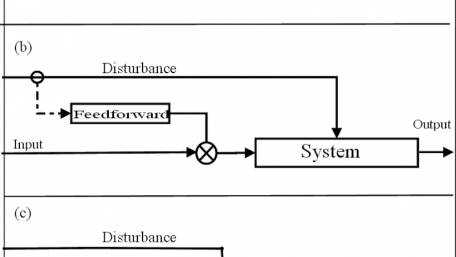
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical…
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical infrastructure in the age of security vulnerabilities
