
Amid continuous cyber threats and ransomware, it is imperative that critical infrastructure data is kept safe. MOXA’s newest router has integrated DPI and VPN…
Amid continuous cyber threats and ransomware, it is imperative that critical infrastructure data is kept safe. MOXA’s newest router has integrated DPI and VPN to help keep data secure.

Fuel cell use is picking up in manufacturing and industrial automation. But what is a fuel cell, how is it different from…
Fuel cell use is picking up in manufacturing and industrial automation. But what is a fuel cell, how is it different from traditional power sources, and what are some common hardware-in-the-loop (HIL) simulation options?
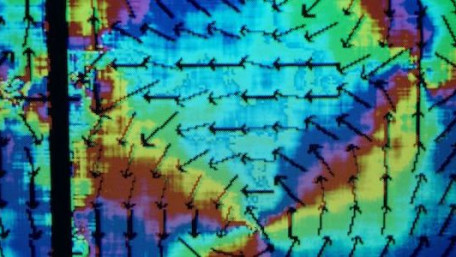
Fluid flow and control are often used in the wastewater, food and beverage, and chemical industries. Which types of…
Fluid flow and control are often used in the wastewater, food and beverage, and chemical industries. Which types of machine learning (ML) algorithms are best suited for fluid dynamics?
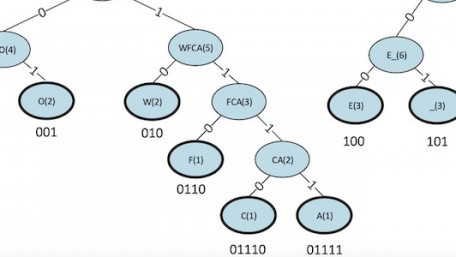
Learn the steps of Huffman coding, a simple and effective lossless data compression algorithm.
Learn the steps of Huffman coding, a simple and effective lossless data compression algorithm.

How can engineers analyze human- and machine-readable data in several industrial applications, such as thermal management…
How can engineers analyze human- and machine-readable data in several industrial applications, such as thermal management and HVAC systems?

The Biden Administration recently released a new statement providing updates regarding its national plan to secure…
The Biden Administration recently released a new statement providing updates regarding its national plan to secure critical infrastructure control systems.

Manufacturing is feeling the crunch of skilled technicians retiring, with nobody to fill their places. A few companies…
Manufacturing is feeling the crunch of skilled technicians retiring, with nobody to fill their places. A few companies and innovation centers are creating pipelines of skilled technicians.
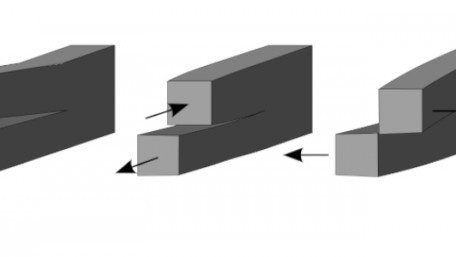
Always cracking your HMI? Learn how fracture mechanics strives to model and understand how cracks form and propagate.
Always cracking your HMI? Learn how fracture mechanics strives to model and understand how cracks form and propagate.

Each industrial revolution has had an impact on factories. Are we going through a fourth revolution?
Each industrial revolution has had an impact on factories. Are we going through a fourth revolution?

Who are some of these major industry leaders and what are their latest efforts in reshoring operations in the United States?
Who are some of these major industry leaders and what are their latest efforts in reshoring operations in the United States?

Algorithms can involve complicated programming. However, they didn’t start out that way. This article dives into basic…
Algorithms can involve complicated programming. However, they didn’t start out that way. This article dives into basic algorithms like sorting and image generation.
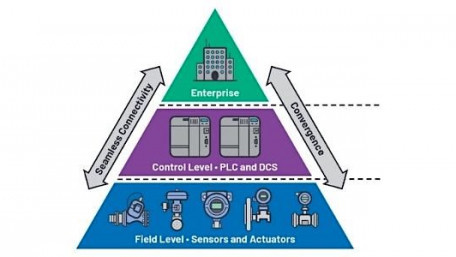
What makes a factory network? There are three levels: device, control, and enterprise. What does each level consist of,…
What makes a factory network? There are three levels: device, control, and enterprise. What does each level consist of, and how is it used in a factory network?
Industrial cybersecurity firm Claroty has launched a new research arm named Team82.
Industrial cybersecurity firm Claroty has launched a new research arm named Team82.

Are wired networks really more secure than wireless? Let’s dive into some differences between these two industrial…
Are wired networks really more secure than wireless? Let’s dive into some differences between these two industrial network types.

Teknic’s entire range of motors is now certified to operate at extremely low and high temperatures.
Teknic’s entire range of motors is now certified to operate at extremely low and high temperatures.
Manufacturing giant Emerson has recently released a new enterprise-level data management software solution.
Manufacturing giant Emerson has recently released a new enterprise-level data management software solution.

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.

In this article, we cover some of the most common HMI failures and troubleshooting methods.
In this article, we cover some of the most common HMI failures and troubleshooting methods.
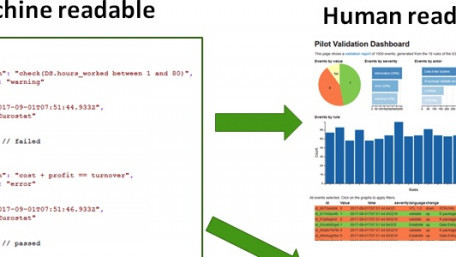
Industrial manufacturers use two main data types—machine-readable and human-readable—to analyze for maintenance,…
Industrial manufacturers use two main data types—machine-readable and human-readable—to analyze for maintenance, monitoring, or other applications.

Dive into the importance of future-proofing IoT technologies, and future trends to keep in mind.
Dive into the importance of future-proofing IoT technologies, and future trends to keep in mind.
