
Converting thermal energy into electrical signals, temperature sensors such as RTDs and thermocouples are fundamental in the maintenance and operation of…
Converting thermal energy into electrical signals, temperature sensors such as RTDs and thermocouples are fundamental in the maintenance and operation of industrial environments and equipment.
A subset of light is the focused cohesive beams that make up lasers, which can be used in optical sensing. These devices…
A subset of light is the focused cohesive beams that make up lasers, which can be used in optical sensing. These devices provide benefits of greater range, precision, and even mapping for mobile robotics.

Cybersecurity is all about processes and people. A lot of threats can be mitigated through technology, but only if people…
Cybersecurity is all about processes and people. A lot of threats can be mitigated through technology, but only if people understand how cybersecurity affects control systems and related technology.

Mitsubishi Electric releases a new module that combines IoT asynchronous messaging with deterministic cyclic messaging…
Mitsubishi Electric releases a new module that combines IoT asynchronous messaging with deterministic cyclic messaging typically found in field I/O.

Industrial sensors can be found in nearly every modern industrial process, regardless of complexity. Learn the history,…
Industrial sensors can be found in nearly every modern industrial process, regardless of complexity. Learn the history, evolution, and variety of sensors that make manufacturing the modern marvel we see today.

ASRock Industrial has introduced a new addition to their IoT controllers. The iEP-5010G is packed with communication and…
ASRock Industrial has introduced a new addition to their IoT controllers. The iEP-5010G is packed with communication and input/outputs for modern IoT controller solutions.

Industrial Ethernet is getting a facelift, but will the industry adopt this new change? Single Pair Ethernet (SPE) offers…
Industrial Ethernet is getting a facelift, but will the industry adopt this new change? Single Pair Ethernet (SPE) offers gigabit speeds with a reduced footprint. When is it used, and where?

Pipelines are used to transport oil and gas safely and efficiently. In this article, we'll explore some technologies…
Pipelines are used to transport oil and gas safely and efficiently. In this article, we'll explore some technologies being used to protect and maintain the integrity of oil and gas pipeline infrastructures.

Machine safety design can be a daunting task with all the different safety devices on the market today. Choosing the…
Machine safety design can be a daunting task with all the different safety devices on the market today. Choosing the correct device for your design can be made easier by understanding when to use the proper device.

We are taught that parallel circuits maintain equal voltage across all branch resistors, equally sharing the source…
We are taught that parallel circuits maintain equal voltage across all branch resistors, equally sharing the source voltage. But reality is often far from ideal, and individual devices certainly impact the rest of the circuit.

Machine learning is a subset of AI that allows a machine to learn using past data. Learn about the two categories of…
Machine learning is a subset of AI that allows a machine to learn using past data. Learn about the two categories of machine learning as well as four major machine learning models often used in industrial applications.

Industrial network switches connect automation equipment, controllers, and other such devices. Learn about unmanaged,…
Industrial network switches connect automation equipment, controllers, and other such devices. Learn about unmanaged, managed, and PoE enabled switches, as well as the differences between switches, routers, and hubs.

With the growing global robotics market, ABB seeks to capitalize on the growing demands by opening a "state-of-the-art"…
With the growing global robotics market, ABB seeks to capitalize on the growing demands by opening a "state-of-the-art" mega factory in Shanghai for manufacturing next-generation robots.

LIDAR technology, critical for mobile robotic and logistic applications, has been the subject of new breakthrough…
LIDAR technology, critical for mobile robotic and logistic applications, has been the subject of new breakthrough research led by Phlux Technology, using innovative materials to solve barriers to progress.

Amazon continues to automate its delivery services, both on the ground and in the air, while global workforces remain…
Amazon continues to automate its delivery services, both on the ground and in the air, while global workforces remain uncertain of whether automation will truly work in their favor.

Learn about proportional gain and proportional band, two key proportional control concepts, to better understand the most…
Learn about proportional gain and proportional band, two key proportional control concepts, to better understand the most popular control system method in industrial automation.

AC motors are common throughout industry - easily controlled by VFDs and without the maintenance that comes with DC…
AC motors are common throughout industry - easily controlled by VFDs and without the maintenance that comes with DC brushes. So then, why are DC motors still used in certain applications?

We've read about the capabilities of collaborative robots, but often, one question still remains - how do you program a…
We've read about the capabilities of collaborative robots, but often, one question still remains - how do you program a cobot? Last week, I got a chance to get my hands on a cobot for the first time.
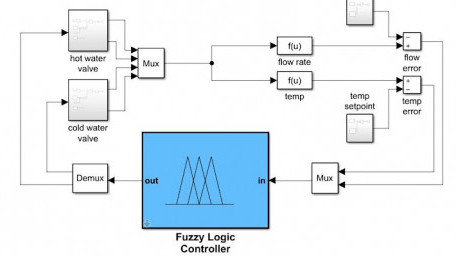
Servo motors are widely utilized in industry for numerous applications. How do you use fuzzy logic to control a servo motor?
Servo motors are widely utilized in industry for numerous applications. How do you use fuzzy logic to control a servo motor?

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.
