
Rockwell Automation announced its partnership with The Water Council to support the advancement of positive water stewardship for corporations around the globe.
Rockwell Automation announced its partnership with The Water Council to support the advancement of positive water stewardship for corporations around the globe.

Programmable Logic Controllers, or PLCs, are designed to receive signals and influence load devices automatically. Learn…
Programmable Logic Controllers, or PLCs, are designed to receive signals and influence load devices automatically. Learn how to connect and program discrete output devices like solenoids, relays, and lights.

Many control product manufacturers offer these downloadable ‘EDS files’ for peripheral equipment, but what exactly is…
Many control product manufacturers offer these downloadable ‘EDS files’ for peripheral equipment, but what exactly is an EDS, and how can they aid in the development of a project?

Despite the many overlaps, PLCs and RTUs are two different devices, each with specific suitable applications.
Despite the many overlaps, PLCs and RTUs are two different devices, each with specific suitable applications.
Control Automation is proud to announce updates to several chapters of our popular online textbook. Check out the…
Control Automation is proud to announce updates to several chapters of our popular online textbook. Check out the improvements in the PLC, Feedback Control, and Power Generation sections.

The control and visualization of power plant processes through SCADA improves the supervision, coordination, and security…
The control and visualization of power plant processes through SCADA improves the supervision, coordination, and security of the power system operations.

Learn the basics of remote terminal units (RTUs) and how they fit into a SCADA system.
Learn the basics of remote terminal units (RTUs) and how they fit into a SCADA system.

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.

What are some considerations and challenges when integrating an HMI into an existing control system? Let’s dive into…
What are some considerations and challenges when integrating an HMI into an existing control system? Let’s dive into the benefits and challenges.

Dive into why protocols are essential in industrial remote monitoring along with the most common types of open protocols…
Dive into why protocols are essential in industrial remote monitoring along with the most common types of open protocols seen in facilities.

This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a…
This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a remote monitoring mechanism.

What kind of guidance is available to help you defend your industrial control system (ICS)?
What kind of guidance is available to help you defend your industrial control system (ICS)?
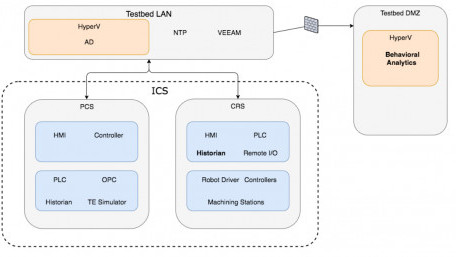
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track…
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track potential security threats.

Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility…
Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility plants protected.

Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the…
Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the solution right in place.

Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the…
Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the operational risks, and how are they assessed?
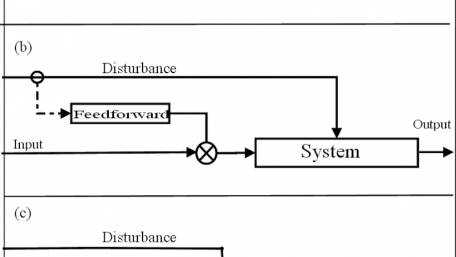
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical…
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical infrastructure in the age of security vulnerabilities
