
Computers understand values as long strings of binary bits, but we humans convert them to other systems for convenience. Decimal makes sense, but what about…
Computers understand values as long strings of binary bits, but we humans convert them to other systems for convenience. Decimal makes sense, but what about hexadecimal and the lesser-known octal systems?

Machine learning is a subset of AI that allows a machine to learn using past data. Learn about the two categories of…
Machine learning is a subset of AI that allows a machine to learn using past data. Learn about the two categories of machine learning as well as four major machine learning models often used in industrial applications.

Industrial network switches connect automation equipment, controllers, and other such devices. Learn about unmanaged,…
Industrial network switches connect automation equipment, controllers, and other such devices. Learn about unmanaged, managed, and PoE enabled switches, as well as the differences between switches, routers, and hubs.

Memory for data is among the most pressing challenges to Industry 4.0. Given the evolving nature of Industry 4.0 and…
Memory for data is among the most pressing challenges to Industry 4.0. Given the evolving nature of Industry 4.0 and associated memory solutions, however, some memory-based trends are becoming apparent.

Human-machine interfaces, or HMIs, provide visual process data and allow access to process parameters and diagnostics…
Human-machine interfaces, or HMIs, provide visual process data and allow access to process parameters and diagnostics information. What’s inside these touchscreen displays, and how do they actually work?

One of the most visible elements of industrial safety is the use of lock-out-tag-out (LOTO) devices, familiar to those…
One of the most visible elements of industrial safety is the use of lock-out-tag-out (LOTO) devices, familiar to those with experience. But, if you are new to the workforce, a brief introduction may be helpful.

Safety is of utmost importance in the day-to-day operations of any system, especially a system where humans and machines…
Safety is of utmost importance in the day-to-day operations of any system, especially a system where humans and machines work together. Learn all about Safety Instrumented Systems and what it takes to keep workers safe, and the system running smoothly!

Due to the robust nature of process industries, there is a vast amount of data to read. Remote access can help parse data…
Due to the robust nature of process industries, there is a vast amount of data to read. Remote access can help parse data and has many additional benefits in these industries.

What are some steps to consider before integrating a cobot, such as Universal Robots, into a facility?
What are some steps to consider before integrating a cobot, such as Universal Robots, into a facility?
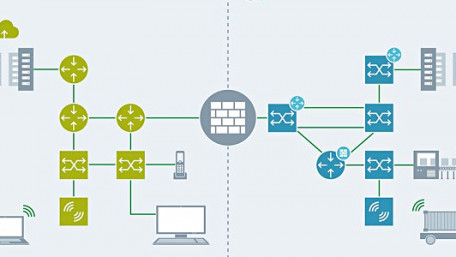
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best…
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best practices.

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.

Dive into why protocols are essential in industrial remote monitoring along with the most common types of open protocols…
Dive into why protocols are essential in industrial remote monitoring along with the most common types of open protocols seen in facilities.

This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a…
This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a remote monitoring mechanism.

Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used…
Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used in industry.
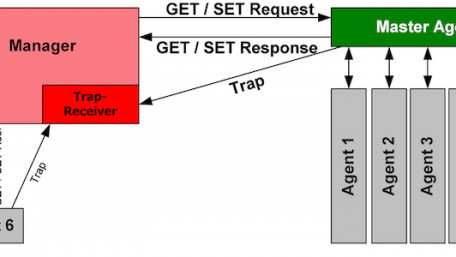
This article discusses common implementations of UPS in control systems and important design considerations.
This article discusses common implementations of UPS in control systems and important design considerations.

What kind of guidance is available to help you defend your industrial control system (ICS)?
What kind of guidance is available to help you defend your industrial control system (ICS)?

What are autonomous mobile robots and how did they come to be a crucial part of the industrial manufacturing industry?
What are autonomous mobile robots and how did they come to be a crucial part of the industrial manufacturing industry?
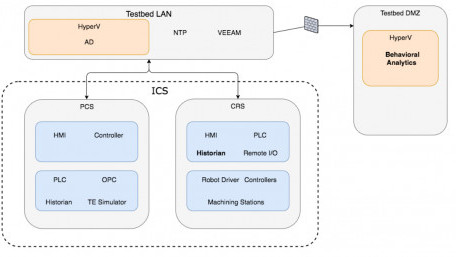
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track…
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track potential security threats.

Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility…
Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility plants protected.

Learn all about Digital Twinning, and how this new technique can change the way we do a number of industrial operations!
Learn all about Digital Twinning, and how this new technique can change the way we do a number of industrial operations!
