
Failures are never the goal of any industrial operation. But when disaster strikes, it’s always better to have a mitigation plan in place well in advance of…
Failures are never the goal of any industrial operation. But when disaster strikes, it’s always better to have a mitigation plan in place well in advance of the event to ensure timely recovery.

No more IIoT buzzwords! This article aims to walk through an implementation of MQTT using the paho-mqtt library using…
No more IIoT buzzwords! This article aims to walk through an implementation of MQTT using the paho-mqtt library using nothing more than your local machine and some simple Python programming.

Cybersecurity is all about processes and people. A lot of threats can be mitigated through technology, but only if people…
Cybersecurity is all about processes and people. A lot of threats can be mitigated through technology, but only if people understand how cybersecurity affects control systems and related technology.

Addressing cybersecurity threats introduced by IIoT technology and devices can quickly seem overwhelming. However, an…
Addressing cybersecurity threats introduced by IIoT technology and devices can quickly seem overwhelming. However, an understanding of the risks can lead to some straightforward countermeasures.

Network routers are designed to route and pass information between a system of connected computers and devices. Learn…
Network routers are designed to route and pass information between a system of connected computers and devices. Learn about the role of routers in industrial applications and how to properly maintain them.

Servers are vital to the flow of information in and around organizations, acting as a hub for information transfer and…
Servers are vital to the flow of information in and around organizations, acting as a hub for information transfer and storage. Learn about the role of servers in industry and the potential challenges that come with maintaining them.

By shaping new concepts and business models, the IIoT is bringing more efficiency and capacity to automated systems. Take…
By shaping new concepts and business models, the IIoT is bringing more efficiency and capacity to automated systems. Take a look at some of the ways the IIoT is revolutionizing the manufacturing and automation sectors.

Over the last decade, cloud service providers have improved technology, particularly data security and integrity. These…
Over the last decade, cloud service providers have improved technology, particularly data security and integrity. These remain the top concern of many manufacturing businesses, but as improvements are rolled out, more and more companies are adopting cloud solutions.

Blockchain recording can reduce risks associated with data transactions such as data theft and erroneous information. But…
Blockchain recording can reduce risks associated with data transactions such as data theft and erroneous information. But what implications, if any, does blockchain hold for industrial control system engineers?

This article covers the definition of warehouse management systems (WMS), describing the basic functions and benefits.
This article covers the definition of warehouse management systems (WMS), describing the basic functions and benefits.

Learn about how blockchain technology works, why it’s secure, and how to use it in industrial automation.
Learn about how blockchain technology works, why it’s secure, and how to use it in industrial automation.
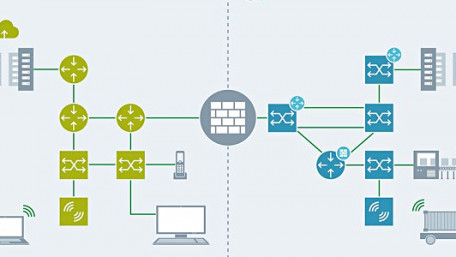
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best…
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best practices.

As IIoT and Industry 4.0 continue to grow, so do its technologies. Machine vision is becoming more widely used in the…
As IIoT and Industry 4.0 continue to grow, so do its technologies. Machine vision is becoming more widely used in the industry, and IIoT pushes it to become more and advanced as time progresses.

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.

This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a…
This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a remote monitoring mechanism.

Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used…
Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used in industry.
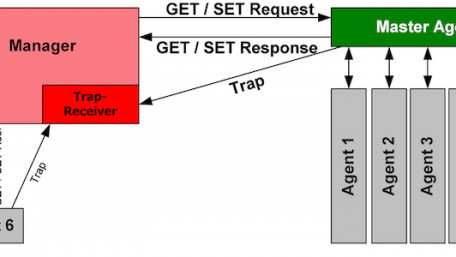
This article discusses common implementations of UPS in control systems and important design considerations.
This article discusses common implementations of UPS in control systems and important design considerations.

Learn about how various types of robots are currently being deployed in the automotive sector and some of the challenges…
Learn about how various types of robots are currently being deployed in the automotive sector and some of the challenges they face on the factory floor.

What kind of guidance is available to help you defend your industrial control system (ICS)?
What kind of guidance is available to help you defend your industrial control system (ICS)?
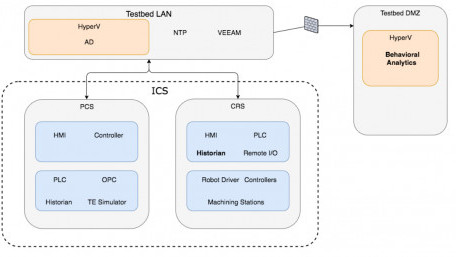
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track…
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track potential security threats.
