
The scope of this article shows one method of writing data to a file using LabVIEW software, and when this type of data acquisition and recording is appropriate.
The scope of this article shows one method of writing data to a file using LabVIEW software, and when this type of data acquisition and recording is appropriate.
Efficient communication between machines is key in industrial automation. As both Ethernet and wireless network…
Efficient communication between machines is key in industrial automation. As both Ethernet and wireless network technologies improve, which one is poised to take the lead in the future?
Fiber optics is a promising technology for the future of industrial automation. In this article, learn the history,…
Fiber optics is a promising technology for the future of industrial automation. In this article, learn the history, fundamentals, and application of fiber optics.
An overview of the requirements, standards, applications, and main differences between Profinet and Profibus…
An overview of the requirements, standards, applications, and main differences between Profinet and Profibus communication protocol, connectors, and evolution from its original technology.

IoT infrastructure consists of many factory parts, one being cloud computing. Rather than ask how they’re different,…
IoT infrastructure consists of many factory parts, one being cloud computing. Rather than ask how they’re different, let’s look into how they work together to form industry 4.0.

In programming languages, loops control processes and instrumentation. Learn how to set up while loops, for loops, and…
In programming languages, loops control processes and instrumentation. Learn how to set up while loops, for loops, and other types of loops in LabVIEW.
New control technology requires new interfaces. How can you implement fuel cell hardware-in-the-loop (HIL) simulations…
New control technology requires new interfaces. How can you implement fuel cell hardware-in-the-loop (HIL) simulations using an HMI?
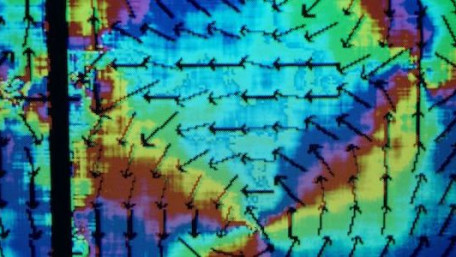
Fluid flow and control are often used in the wastewater, food and beverage, and chemical industries. Which types of…
Fluid flow and control are often used in the wastewater, food and beverage, and chemical industries. Which types of machine learning (ML) algorithms are best suited for fluid dynamics?
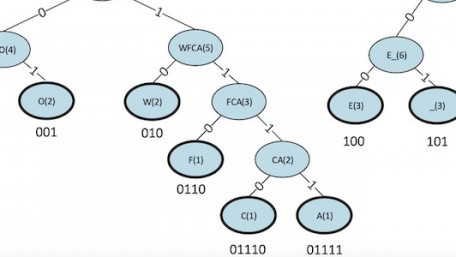
Learn the steps of Huffman coding, a simple and effective lossless data compression algorithm.
Learn the steps of Huffman coding, a simple and effective lossless data compression algorithm.

How can engineers analyze human- and machine-readable data in several industrial applications, such as thermal management…
How can engineers analyze human- and machine-readable data in several industrial applications, such as thermal management and HVAC systems?

Each industrial revolution has had an impact on factories. Are we going through a fourth revolution?
Each industrial revolution has had an impact on factories. Are we going through a fourth revolution?

Algorithms can involve complicated programming. However, they didn’t start out that way. This article dives into basic…
Algorithms can involve complicated programming. However, they didn’t start out that way. This article dives into basic algorithms like sorting and image generation.
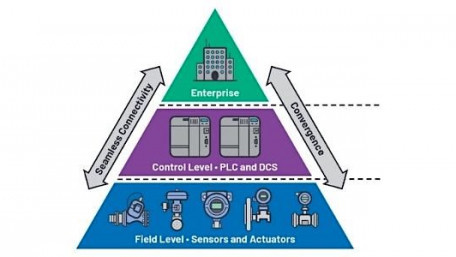
What makes a factory network? There are three levels: device, control, and enterprise. What does each level consist of,…
What makes a factory network? There are three levels: device, control, and enterprise. What does each level consist of, and how is it used in a factory network?

Are wired networks really more secure than wireless? Let’s dive into some differences between these two industrial…
Are wired networks really more secure than wireless? Let’s dive into some differences between these two industrial network types.

Learn about the evolution of industrial-level communications networking, and current and future protocols.
Learn about the evolution of industrial-level communications networking, and current and future protocols.

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.

In this article, we cover some of the most common HMI failures and troubleshooting methods.
In this article, we cover some of the most common HMI failures and troubleshooting methods.
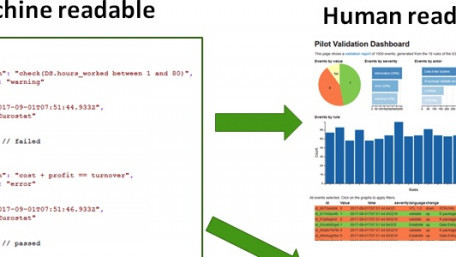
Industrial manufacturers use two main data types—machine-readable and human-readable—to analyze for maintenance,…
Industrial manufacturers use two main data types—machine-readable and human-readable—to analyze for maintenance, monitoring, or other applications.
When programming large virtual instruments (VIs) in LabVIEW, it may be useful to create and call a sub-VI to enhance…
When programming large virtual instruments (VIs) in LabVIEW, it may be useful to create and call a sub-VI to enhance readability and delegation.

Learn the differences and similarities between human-machine interface (HMI) and supervisory control and data acquisition…
Learn the differences and similarities between human-machine interface (HMI) and supervisory control and data acquisition (SCADA) and how they work together.
