
This article will provide an overview of Rockwell's library of process objects programming instructions and faceplates and how they are used.
This article will provide an overview of Rockwell's library of process objects programming instructions and faceplates and how they are used.
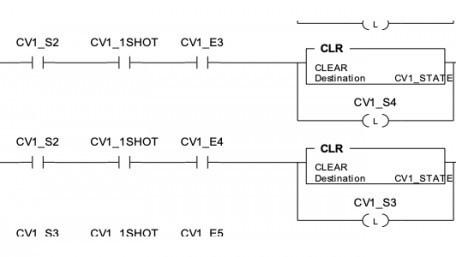
The need for sequential control logic is frequently required for machine control. State machine programming is a powerful…
The need for sequential control logic is frequently required for machine control. State machine programming is a powerful technique that can be layered on traditional ladder logic to satisfy this need.

Building Automation and Control Network (BACnet) is commonly used in building automation systems. Learn how the BACnet…
Building Automation and Control Network (BACnet) is commonly used in building automation systems. Learn how the BACnet protocol works and the different network technology used to set up the system.

The benefits of modern building automation systems (BAS) include interoperability and technical support in case a problem…
The benefits of modern building automation systems (BAS) include interoperability and technical support in case a problem occurs. Learn about the BAS four-layer architecture concept adopted by manufacturers.

Building automation systems (BAS) control the environmental parameters of a factory. In this article, learn about the…
Building automation systems (BAS) control the environmental parameters of a factory. In this article, learn about the requirements and components of a BAS.

Learn about the importance of the ISO 9001 standard and some essential procedures and considerations to make when using…
Learn about the importance of the ISO 9001 standard and some essential procedures and considerations to make when using the standard.

A computerized maintenance management system (CMMS) is a software system that manages an entire company’s…
A computerized maintenance management system (CMMS) is a software system that manages an entire company’s maintenance activities. It supports the maintenance personnel by helping to develop a database relevant to maintenance activities.
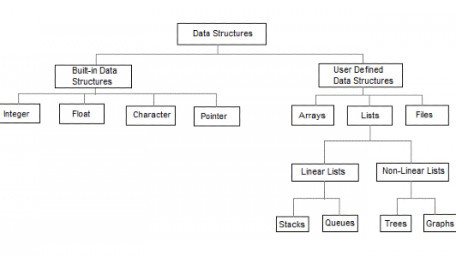
This article discusses structure data types, structure tags, and various applications of user-defined structures.
This article discusses structure data types, structure tags, and various applications of user-defined structures.
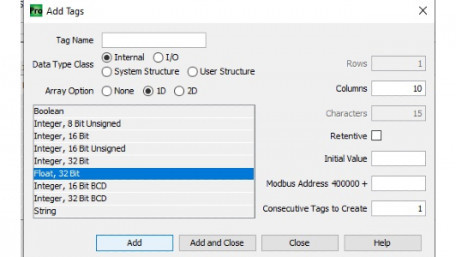
In this article, we’ll investigate the meaning of an array, but also explore some of the ways in which arrays can be…
In this article, we’ll investigate the meaning of an array, but also explore some of the ways in which arrays can be used specifically within the context of a PLC system.
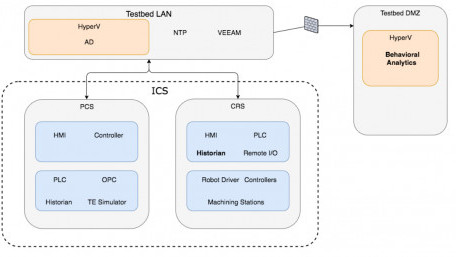
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track…
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track potential security threats.

Two of the most common protocols are Modbus and Profinet. They are similar in many ways, but there are some crucial differences.
Two of the most common protocols are Modbus and Profinet. They are similar in many ways, but there are some crucial differences.

This article discusses several different types of NEMA enclosure ratings and which one may be the right one for your…
This article discusses several different types of NEMA enclosure ratings and which one may be the right one for your specific applications.
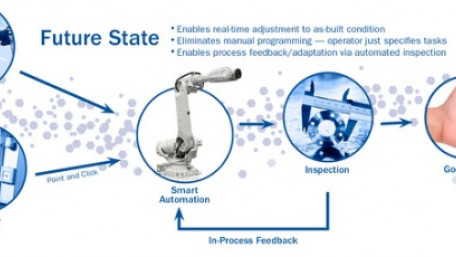
Learn about Robot Operating System Industrial (ROS-I) an open-source middleware framework for robotics used in industrial…
Learn about Robot Operating System Industrial (ROS-I) an open-source middleware framework for robotics used in industrial manufacturing.

Manufacturing plants must follow certain safety protocols set to them by governing bodies in their countries. Learn about…
Manufacturing plants must follow certain safety protocols set to them by governing bodies in their countries. Learn about key verification protocols (IQ, OQ, and PQ) and how to properly set up a verification master plan.

Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility…
Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility plants protected.

Take a trip down memory lane and go through the different communication systems used throughout the years and learn about…
Take a trip down memory lane and go through the different communication systems used throughout the years and learn about the factors that led to where we are today.
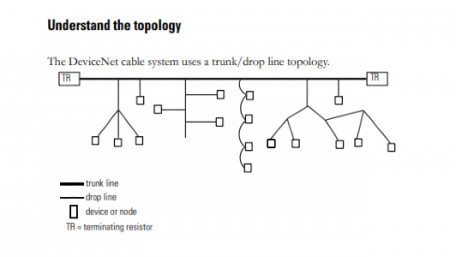
Ethernet is everywhere. It’s simple and easy to use, so why are DeviceNet and ControlNet still here?
Ethernet is everywhere. It’s simple and easy to use, so why are DeviceNet and ControlNet still here?
Learn about the supervisory control and data acquisition system used to program PLCs and PIDs. See where, how, and why…
Learn about the supervisory control and data acquisition system used to program PLCs and PIDs. See where, how, and why SCADA systems are so popular.

Within an industrial setting, noise from EMI can create huge problems. For large load devices using many amps of current,…
Within an industrial setting, noise from EMI can create huge problems. For large load devices using many amps of current, small electrical noise may not be too critical. But when it comes to low-voltage and low-current communication wires, just a small amount of voltage finding its way onto a wire can corrupt data transmissions. Shielded cables can help to protect against that problem.

This article covers how predictive and preventive maintenance work, the types of each form of maintenance, and…
This article covers how predictive and preventive maintenance work, the types of each form of maintenance, and applications in which each is used.
