
American history has undergone several industrial revolutions largely focused on mass production. Are we heading into a fifth revolution focused on human-machine…
American history has undergone several industrial revolutions largely focused on mass production. Are we heading into a fifth revolution focused on human-machine interaction?

What does “digital transformation” really mean, and what are the technologies involved in the process? Further, which…
What does “digital transformation” really mean, and what are the technologies involved in the process? Further, which of these technologies are facilities adopting?

Data science is a multidisciplinary field crucial to modern automation. In this article, learn about data science…
Data science is a multidisciplinary field crucial to modern automation. In this article, learn about data science concepts and best practices.

Learn the fundaments of data lakes and how they are important to digital transformation under Industry 4.0.
Learn the fundaments of data lakes and how they are important to digital transformation under Industry 4.0.

IoT infrastructure consists of many factory parts, one being cloud computing. Rather than ask how they’re different,…
IoT infrastructure consists of many factory parts, one being cloud computing. Rather than ask how they’re different, let’s look into how they work together to form industry 4.0.
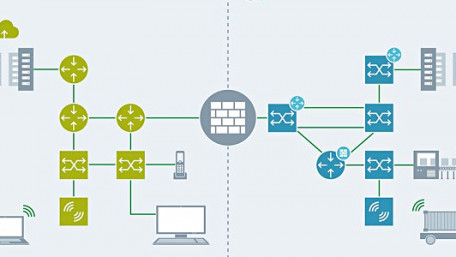
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best…
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best practices.

As IIoT and Industry 4.0 continue to grow, so do its technologies. Machine vision is becoming more widely used in the…
As IIoT and Industry 4.0 continue to grow, so do its technologies. Machine vision is becoming more widely used in the industry, and IIoT pushes it to become more and advanced as time progresses.

Each industrial revolution has had an impact on factories. Are we going through a fourth revolution?
Each industrial revolution has had an impact on factories. Are we going through a fourth revolution?

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.

Learn the differences and similarities between human-machine interface (HMI) and supervisory control and data acquisition…
Learn the differences and similarities between human-machine interface (HMI) and supervisory control and data acquisition (SCADA) and how they work together.

What are some considerations and challenges when integrating an HMI into an existing control system? Let’s dive into…
What are some considerations and challenges when integrating an HMI into an existing control system? Let’s dive into the benefits and challenges.

This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a…
This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a remote monitoring mechanism.

What kind of guidance is available to help you defend your industrial control system (ICS)?
What kind of guidance is available to help you defend your industrial control system (ICS)?

The following will introduce how machine vision and object recognition works and how developers are working on making it…
The following will introduce how machine vision and object recognition works and how developers are working on making it easier to integrate for more extensive market adoption.
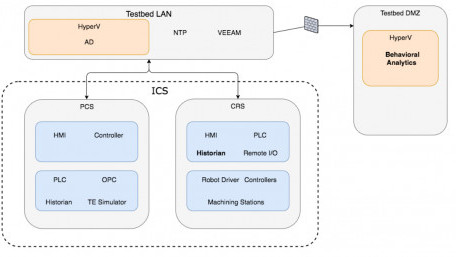
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track…
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track potential security threats.
As digital twinning technology continues to advance, industry leaders are stepping up their innovation efforts to bring…
As digital twinning technology continues to advance, industry leaders are stepping up their innovation efforts to bring together the physical and virtual world.
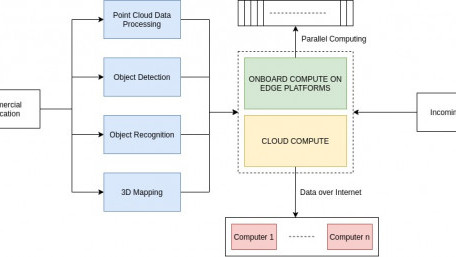
Edge computing and cloud computing both have their place in industrial automation and control systems. Learn about the…
Edge computing and cloud computing both have their place in industrial automation and control systems. Learn about the uses and how far the two technologies have to go before they're universally adopted.

Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility…
Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility plants protected.

Learn all about Digital Twinning, and how this new technique can change the way we do a number of industrial operations!
Learn all about Digital Twinning, and how this new technique can change the way we do a number of industrial operations!

Liquid lens and multi-spectral lighting solutions are advancing the manufacturer’s production lines.
Liquid lens and multi-spectral lighting solutions are advancing the manufacturer’s production lines.
