
A walkthrough and discussion of a simple web-based HMI solution that could modernize your current HMI technology stack. The first step in the process involves…
A walkthrough and discussion of a simple web-based HMI solution that could modernize your current HMI technology stack. The first step in the process involves sending data from a device to a server.

Control.com’s Director of Engineering got to explore IO-Link sensors and what he found might surprise you! Although…
Control.com’s Director of Engineering got to explore IO-Link sensors and what he found might surprise you! Although still considered an “emerging” technology, it’s clear IO-Link technology boasts several bonafide benefits over traditional sensors.

Refining and integrating a front-end HMI application to an API middle layer with real-time data display and historian…
Refining and integrating a front-end HMI application to an API middle layer with real-time data display and historian capabilities for short-term data visualization.

Learn the first steps in focusing on the integration of a front-end HMI application to an API middle layer.
Learn the first steps in focusing on the integration of a front-end HMI application to an API middle layer.

The middle layer, or API layer of a custom-built HMI project involves a server that can submit or receive data to and…
The middle layer, or API layer of a custom-built HMI project involves a server that can submit or receive data to and from a device, either to provide the user interface or interact with the machine.

Many articles address the wiring and implementation of analog control signals, but where are they used, and what might…
Many articles address the wiring and implementation of analog control signals, but where are they used, and what might make them a better (or perhaps worse) decision than digital input/output devices?

Virtual networks can connect or isolate various local control networks through configuration of a managed switch. Why…
Virtual networks can connect or isolate various local control networks through configuration of a managed switch. Why would we use VLANs, and how can you segment a network switch to create a VLAN?

I could run down to the local box store or internet marketplace and buy a 5-port switch for less than 20 dollars, or…
I could run down to the local box store or internet marketplace and buy a 5-port switch for less than 20 dollars, or invest in an industrial switch for hundreds. Why would I choose the industrial switch?

An introduction to the various tag types used within one of the leading supervisory control and data acquisition (SCADA)…
An introduction to the various tag types used within one of the leading supervisory control and data acquisition (SCADA) software powering IIoT, HMI, and I4.0 applications: Ignition by Inductive Automation.
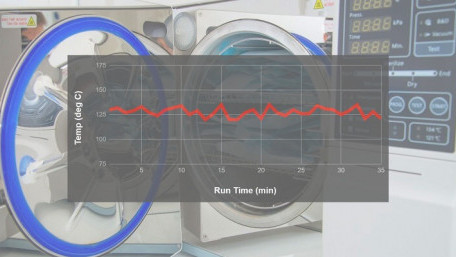
Temperature profiling is an effective tool to monitor thermal properties in process equipment. This article defines…
Temperature profiling is an effective tool to monitor thermal properties in process equipment. This article defines temperature profiling, discusses the process components, and describes the various benefits it offers.
Errors in communications often manifest as a result of electrical noise interrupting the data during the transmission…
Errors in communications often manifest as a result of electrical noise interrupting the data during the transmission process, leading to various methods for determining whether received data has been damaged.

Learn how to build a machine learning model to predict failure classification based on machine parameters using a…
Learn how to build a machine learning model to predict failure classification based on machine parameters using a synthetic dataset modeled after a milling machine, the same process used in real-world systems.
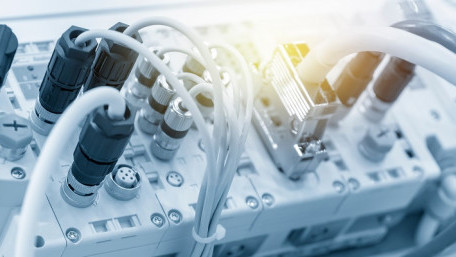
Industrial and robotics cabling requires specialized termination strategies. This article introduces connectors involved…
Industrial and robotics cabling requires specialized termination strategies. This article introduces connectors involved in automation applications for cable-to-cable or cable-to-device termination.

Any kind of computer programming can be challenging to determine what aspects are truly unique versus what aspects should…
Any kind of computer programming can be challenging to determine what aspects are truly unique versus what aspects should be standardized across projects and platforms to streamline future development.
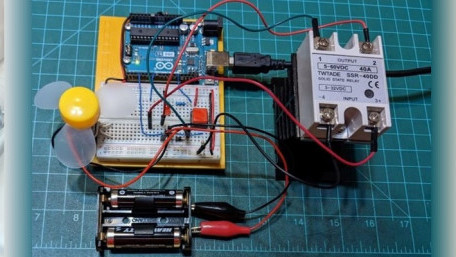
Variable control allows external conditions, like temperature, to be monitored so the controller can activate devices to…
Variable control allows external conditions, like temperature, to be monitored so the controller can activate devices to heat or cool the system as needed. Simulate a temp controller with low-cost components!

Arduino’s Opta mini PLC platform is supported by the new PLC IDE. Learn to create and download your first program and…
Arduino’s Opta mini PLC platform is supported by the new PLC IDE. Learn to create and download your first program and take advantage of built-in I/O for an easy introduction to the platform.

No more IIoT buzzwords! This article aims to walk through an implementation of MQTT using the paho-mqtt library using…
No more IIoT buzzwords! This article aims to walk through an implementation of MQTT using the paho-mqtt library using nothing more than your local machine and some simple Python programming.

Learn about the history, framework, and current uses of the Open Platform Communications United Architecture (OPC UA)…
Learn about the history, framework, and current uses of the Open Platform Communications United Architecture (OPC UA) communication protocol in industrial automation.

The subject of grounding in electronics is broad and complex, spanning across a variety of functions and objectives. In…
The subject of grounding in electronics is broad and complex, spanning across a variety of functions and objectives. In this article, we will investigate the applications and regulation of grounding in control systems on a fundamental level.

Addressing cybersecurity threats introduced by IIoT technology and devices can quickly seem overwhelming. However, an…
Addressing cybersecurity threats introduced by IIoT technology and devices can quickly seem overwhelming. However, an understanding of the risks can lead to some straightforward countermeasures.
