
This article looks at rotary encoders, covering the main types, introducing their characteristics, and introducing their key applications in control systems.
This article looks at rotary encoders, covering the main types, introducing their characteristics, and introducing their key applications in control systems.

When it comes to electrical grounding, many strategies are employed to accomplish different tasks. One of the main…
When it comes to electrical grounding, many strategies are employed to accomplish different tasks. One of the main reasons for grounding equipment is for the safety of users and equipment while maintaining strict adherence to regulations.
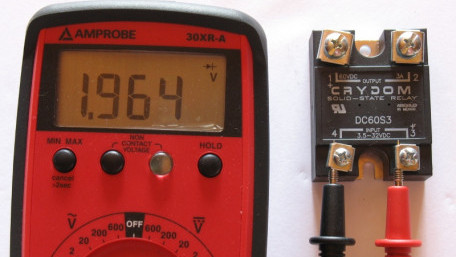
This article discusses some methods for troubleshooting solid-state relays and input/output terminals.
This article discusses some methods for troubleshooting solid-state relays and input/output terminals.
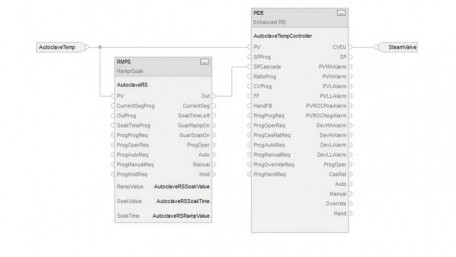
This article will focus on using an Allen-Bradley ramp/soak controller with a PID.
This article will focus on using an Allen-Bradley ramp/soak controller with a PID.

In this article, we take a look at hydraulic, pneumatic, and electric actuators and how they are used in different scenarios.
In this article, we take a look at hydraulic, pneumatic, and electric actuators and how they are used in different scenarios.

Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the…
Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the solution right in place.

Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the…
Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the operational risks, and how are they assessed?
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical…
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical infrastructure in the age of security vulnerabilities
