
For many manufacturing processes, it is extremely important to measure the exact rate at which fluid is moving or flowing. We turn to flow gauges to provide…
For many manufacturing processes, it is extremely important to measure the exact rate at which fluid is moving or flowing. We turn to flow gauges to provide these measurements, and there is a great diversity in operating principle as well as proper application to the fluid that is being measured.
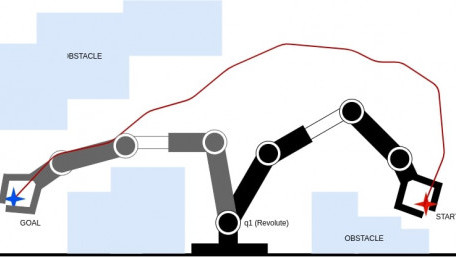
Learn all about visual servoing and motion planning to create an autonomous robot!
Learn all about visual servoing and motion planning to create an autonomous robot!

A common difference of terms arises when referring to air or pneumatic pressure, and those are gauge (BarG) pressure and…
A common difference of terms arises when referring to air or pneumatic pressure, and those are gauge (BarG) pressure and absolute (BarA) pressure. Both can accurately describe a system, but when performing calculations and tests, it’s important to distinguish the difference.

Learn all about user requirement specifications (URS), including what should and should not be included and their…
Learn all about user requirement specifications (URS), including what should and should not be included and their importance for organizations planning to purchase new equipment.

When it comes to electrical grounding, many strategies are employed to accomplish different tasks. One of the main…
When it comes to electrical grounding, many strategies are employed to accomplish different tasks. One of the main reasons for grounding equipment is for the safety of users and equipment while maintaining strict adherence to regulations.
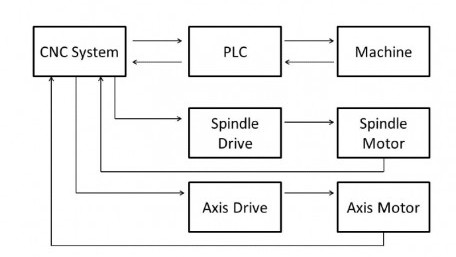
This article discusses the definition of automated drilling and a look into some of the key features and best practices.
This article discusses the definition of automated drilling and a look into some of the key features and best practices.

Are smart devices opening production to attacks? This article provides several tips to ensure your facility is staying…
Are smart devices opening production to attacks? This article provides several tips to ensure your facility is staying smart and safe.
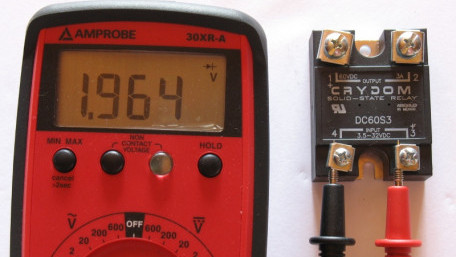
This article discusses some methods for troubleshooting solid-state relays and input/output terminals.
This article discusses some methods for troubleshooting solid-state relays and input/output terminals.

Regardless of industry, codes and standards developed by organizations including ISO, ANSI, and IEEE are an integral part…
Regardless of industry, codes and standards developed by organizations including ISO, ANSI, and IEEE are an integral part of the environment in which we work and have a major influence on engineering and design.

This article provides an introduction to proximity and distance sensors and common uses for them.
This article provides an introduction to proximity and distance sensors and common uses for them.

In this article, we take a look at hydraulic, pneumatic, and electric actuators and how they are used in different scenarios.
In this article, we take a look at hydraulic, pneumatic, and electric actuators and how they are used in different scenarios.

Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the…
Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the solution right in place.

Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the…
Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the operational risks, and how are they assessed?
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical…
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical infrastructure in the age of security vulnerabilities
