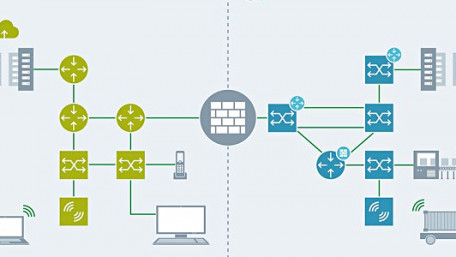
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best practices.
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best practices.
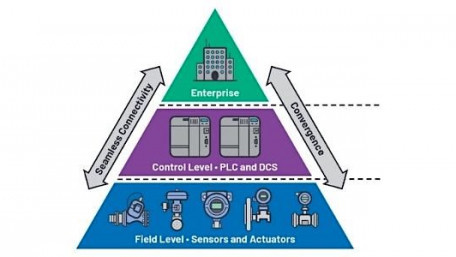
What makes a factory network? There are three levels: device, control, and enterprise. What does each level consist of,…
What makes a factory network? There are three levels: device, control, and enterprise. What does each level consist of, and how is it used in a factory network?
Trying to design industrial HVAC systems in AutoCAD? In this article, we explore AutoDesk’s flagship softwares AutoCAD…
Trying to design industrial HVAC systems in AutoCAD? In this article, we explore AutoDesk’s flagship softwares AutoCAD and Revit, and their role in the HVAC designing industry.

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.

Learn the differences and similarities between human-machine interface (HMI) and supervisory control and data acquisition…
Learn the differences and similarities between human-machine interface (HMI) and supervisory control and data acquisition (SCADA) and how they work together.

Dive into why protocols are essential in industrial remote monitoring along with the most common types of open protocols…
Dive into why protocols are essential in industrial remote monitoring along with the most common types of open protocols seen in facilities.

This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a…
This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a remote monitoring mechanism.

Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used…
Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used in industry.
This article discusses common implementations of UPS in control systems and important design considerations.
This article discusses common implementations of UPS in control systems and important design considerations.

What kind of guidance is available to help you defend your industrial control system (ICS)?
What kind of guidance is available to help you defend your industrial control system (ICS)?

Distributed control systems (DCS) evolved out of control systems for facilities, but their scope can be difficult to…
Distributed control systems (DCS) evolved out of control systems for facilities, but their scope can be difficult to fully understand. This article explores the role of a DCS and how it fits in with PLCs and PACs.
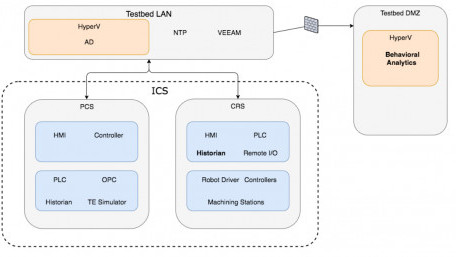
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track…
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track potential security threats.

Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility…
Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility plants protected.

Learn all about Digital Twinning, and how this new technique can change the way we do a number of industrial operations!
Learn all about Digital Twinning, and how this new technique can change the way we do a number of industrial operations!

Learn how one engineer's real-world experience showed him the importance and power of SCADA systems for control automation.
Learn how one engineer's real-world experience showed him the importance and power of SCADA systems for control automation.
Learn about the supervisory control and data acquisition system used to program PLCs and PIDs. See where, how, and why…
Learn about the supervisory control and data acquisition system used to program PLCs and PIDs. See where, how, and why SCADA systems are so popular.

Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the…
Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the solution right in place.

Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the…
Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the operational risks, and how are they assessed?
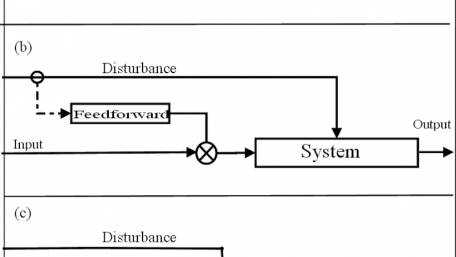
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical…
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical infrastructure in the age of security vulnerabilities
