
Ethernet switches can use four different types of connections: RJ45, fiber, M12, and SFP. Understanding the difference can help with network troubleshooting,…
Ethernet switches can use four different types of connections: RJ45, fiber, M12, and SFP. Understanding the difference can help with network troubleshooting, design, or alteration.

Transformerless UPS designs are taking place in various industries, particularly in aseptic manufacturing,…
Transformerless UPS designs are taking place in various industries, particularly in aseptic manufacturing, pharmaceuticals, and healthcare, where the reliability of power supply is critical.
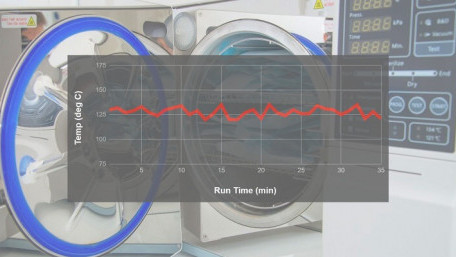
Temperature profiling is an effective tool to monitor thermal properties in process equipment. This article defines…
Temperature profiling is an effective tool to monitor thermal properties in process equipment. This article defines temperature profiling, discusses the process components, and describes the various benefits it offers.

Radiation, despite its reputation in pop culture as a harmful emission resulting from a natural disaster, is a property…
Radiation, despite its reputation in pop culture as a harmful emission resulting from a natural disaster, is a property of many materials and processes and must be carefully monitored for quality and safety.
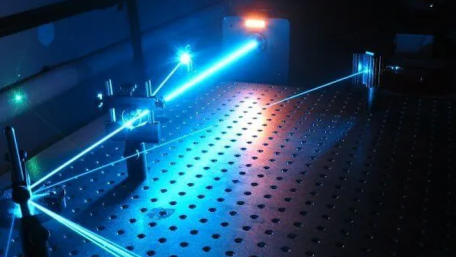
A subset of light is the focused cohesive beams that make up lasers, which can be used in optical sensing. These devices…
A subset of light is the focused cohesive beams that make up lasers, which can be used in optical sensing. These devices provide benefits of greater range, precision, and even mapping for mobile robotics.

Industrial sensors can be found in nearly every modern industrial process, regardless of complexity. Learn the history,…
Industrial sensors can be found in nearly every modern industrial process, regardless of complexity. Learn the history, evolution, and variety of sensors that make manufacturing the modern marvel we see today.

Addressing cybersecurity threats introduced by IIoT technology and devices can quickly seem overwhelming. However, an…
Addressing cybersecurity threats introduced by IIoT technology and devices can quickly seem overwhelming. However, an understanding of the risks can lead to some straightforward countermeasures.

Machine learning is a subset of AI that allows a machine to learn using past data. Learn about the two categories of…
Machine learning is a subset of AI that allows a machine to learn using past data. Learn about the two categories of machine learning as well as four major machine learning models often used in industrial applications.
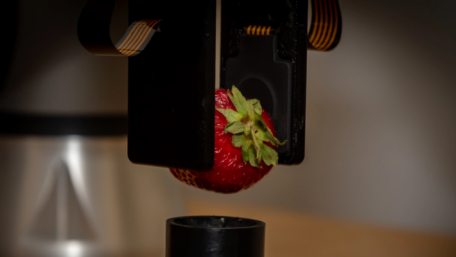
Using advanced sensing technology, robotic skin allows grippers and manipulators to “feel” and handle objects without…
Using advanced sensing technology, robotic skin allows grippers and manipulators to “feel” and handle objects without damaging them. While emulating human touch is still in its infancy, it does show promise for future applications.

Robots are no longer unanimously just "robots"—there are specific tasks and functionality of each kind. Learn about the…
Robots are no longer unanimously just "robots"—there are specific tasks and functionality of each kind. Learn about the technology differences between fixed-location robots and mobile robots and why no one robot is like another.

Redundancy and safety are often seen together in industrial safety systems. Safety relays monitor emergency devices to…
Redundancy and safety are often seen together in industrial safety systems. Safety relays monitor emergency devices to switch contacts based on status - but what makes them different from normal relays?

Moisture inside industrial pneumatic systems is a major cause for concern, and if the air is not filtered or dried…
Moisture inside industrial pneumatic systems is a major cause for concern, and if the air is not filtered or dried properly, it can lead to serious failures.

Safety is of utmost importance in the day-to-day operations of any system, especially a system where humans and machines…
Safety is of utmost importance in the day-to-day operations of any system, especially a system where humans and machines work together. Learn all about Safety Instrumented Systems and what it takes to keep workers safe, and the system running smoothly!

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.

This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a…
This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a remote monitoring mechanism.

Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used…
Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used in industry.
This article discusses common implementations of UPS in control systems and important design considerations.
This article discusses common implementations of UPS in control systems and important design considerations.
Start learning about robotic arm solution, kinematic chain and motion planning, in this first technical installment.
Start learning about robotic arm solution, kinematic chain and motion planning, in this first technical installment.

Learn about safety in LiDAR sensors from different perspectives and some safety-rated applications.
Learn about safety in LiDAR sensors from different perspectives and some safety-rated applications.

What kind of guidance is available to help you defend your industrial control system (ICS)?
What kind of guidance is available to help you defend your industrial control system (ICS)?
