
Is it best to ‘controller scope’ or ‘program scope’ your tags? This is the question asked by many new PLC programmers, and it often comes down to…
Is it best to ‘controller scope’ or ‘program scope’ your tags? This is the question asked by many new PLC programmers, and it often comes down to personal preference.
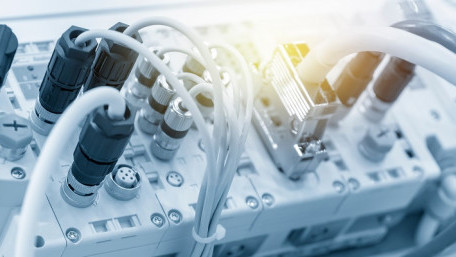
Industrial and robotics cabling requires specialized termination strategies. This article introduces connectors involved…
Industrial and robotics cabling requires specialized termination strategies. This article introduces connectors involved in automation applications for cable-to-cable or cable-to-device termination.

Any kind of computer programming can be challenging to determine what aspects are truly unique versus what aspects should…
Any kind of computer programming can be challenging to determine what aspects are truly unique versus what aspects should be standardized across projects and platforms to streamline future development.

Addressing cybersecurity threats introduced by IIoT technology and devices can quickly seem overwhelming. However, an…
Addressing cybersecurity threats introduced by IIoT technology and devices can quickly seem overwhelming. However, an understanding of the risks can lead to some straightforward countermeasures.

Insufficient controller memory can result in reduced HMI and SCADA response speed and longer scan times. Know the…
Insufficient controller memory can result in reduced HMI and SCADA response speed and longer scan times. Know the differences between RAM, ROM, and removable memory, and how to keep program sizes in check.

Many control product manufacturers offer these downloadable ‘EDS files’ for peripheral equipment, but what exactly is…
Many control product manufacturers offer these downloadable ‘EDS files’ for peripheral equipment, but what exactly is an EDS, and how can they aid in the development of a project?
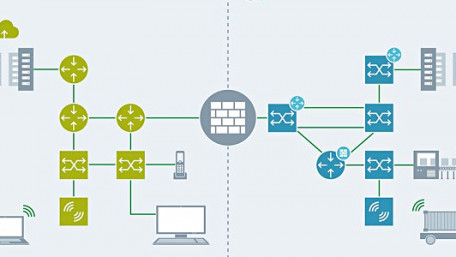
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best…
Centralized and decentralized computing have different cybersecurity needs. Let’s review the differences and some best practices.

IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this…
IIoT infrastructure is more susceptible to cyber-attacks than legacy infrastructure due to its cloud-based nature; this article covers attack vectors and best mitigating practices.

What are some considerations and challenges when integrating an HMI into an existing control system? Let’s dive into…
What are some considerations and challenges when integrating an HMI into an existing control system? Let’s dive into the benefits and challenges.

This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a…
This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a remote monitoring mechanism.

Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used…
Learn about the different types of industrial remote monitoring and some of the various remote monitoring processes used in industry.
This article discusses common implementations of UPS in control systems and important design considerations.
This article discusses common implementations of UPS in control systems and important design considerations.

A brief overview of controllers through history and an analysis of factors to consider when deciding which one to use.
A brief overview of controllers through history and an analysis of factors to consider when deciding which one to use.

This article offers a brief review of types of controllers through history and an analysis of factors to consider when…
This article offers a brief review of types of controllers through history and an analysis of factors to consider when deciding what to use.

Learn about the fundamentals of industrial PCs (IPCs), including their common types and architecture, advantages, and…
Learn about the fundamentals of industrial PCs (IPCs), including their common types and architecture, advantages, and trends happening in their development.

What kind of guidance is available to help you defend your industrial control system (ICS)?
What kind of guidance is available to help you defend your industrial control system (ICS)?
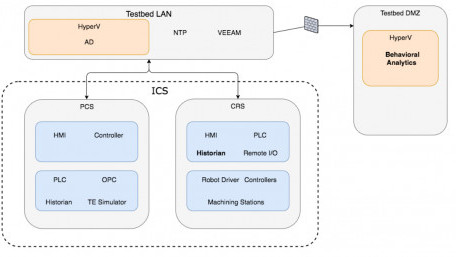
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track…
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track potential security threats.
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical…
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical infrastructure in the age of security vulnerabilities
