
Dive into why protocols are essential in industrial remote monitoring along with the most common types of open protocols seen in facilities.
Dive into why protocols are essential in industrial remote monitoring along with the most common types of open protocols seen in facilities.

This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a…
This article in our continuing series about remote monitoring covers equipment and devices necessary to establish a remote monitoring mechanism.

What kind of guidance is available to help you defend your industrial control system (ICS)?
What kind of guidance is available to help you defend your industrial control system (ICS)?
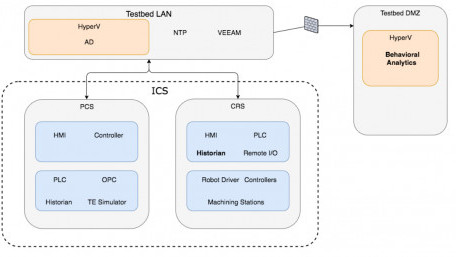
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track…
The latest report from NIST and other government organizations found that tracking behavior may be a new way to track potential security threats.

Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility…
Learn about the many ways cyber-attacks threaten SCADA systems, and what can be done to keep manufacturing and utility plants protected.

Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the…
Networked remote I/O allows us to work with a machine center separately from the rest of the system, and drop the solution right in place.

Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the…
Industrial control system cybersecurity can be a matter of vital corporate and national interest. What are the operational risks, and how are they assessed?
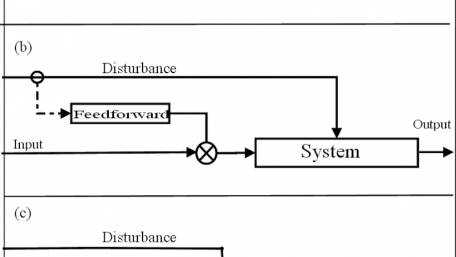
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical…
Take a look at the concept of cyber resilience in control systems and how it relates to cybersecurity for critical infrastructure in the age of security vulnerabilities
